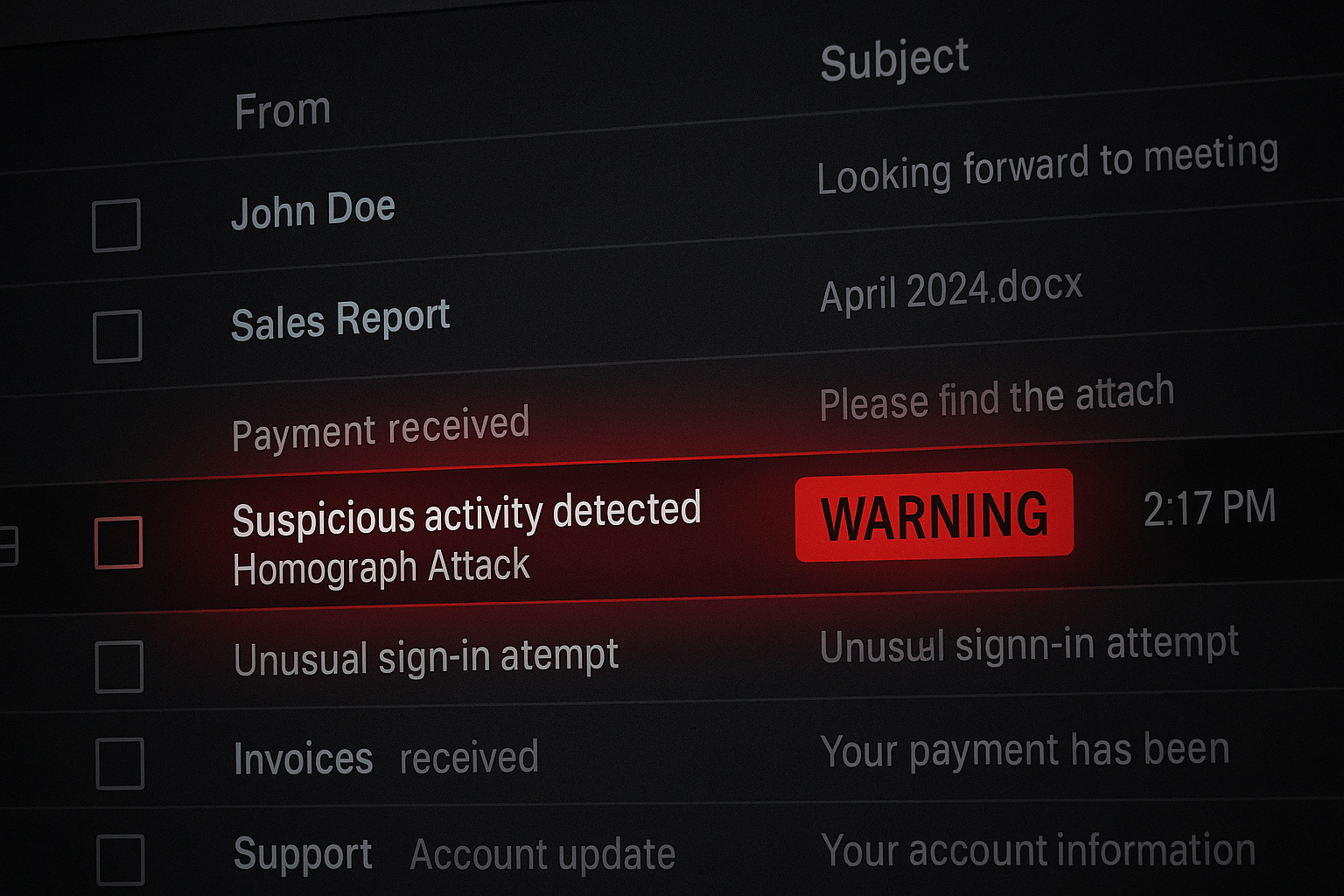
Threat actors are increasingly using homograph attacks — swapping Latin characters with visually similar Cyrillic, Greek or other Unicode characters — to trick recipients and bypass email security filters. A Palo Alto Networks report highlights real-world cases where attackers impersonated trusted brands and services such as Google Drive, DocuSign and Spotify. These emails contained manipulated display names, subjects and links, making them appear legitimate while redirecting victims to attacker-controlled websites designed for credential theft or malware delivery. The rise of AI-generated phishing campaigns has further amplified the threat, allowing attackers to create convincing and highly targeted emails at scale. Security researchers note that while such attacks evade traditional content analysis, they can be detected through careful Unicode inspection, stronger phishing-resistant multi-factor authentication, and enhanced email filtering. Palo Alto Networks recommends advanced email security tools, awareness training, and strict verification practices to mitigate these sophisticated phishing attempts.